All opinion articles are the opinion of the author and not necessarily of American Military News. If you are interested in submitting an op-ed please email [email protected]
[starbox]
It is generally agreed that the writing of language was invented in ancient Sumer, Mesopotamia around 3200 BC. I’m quite certain that the requirement for codes and secret languages followed soon after. Soldiers, spies, and even businessmen have a requirement for clandestine communications. Over the centuries, millions of ciphers and codes have emerged. The intent of this article is to explore three basic types of codes and the principles that drive them.
The earliest codes would have involved a simple letter substitution, or mono alphabetic substitution, where either each letter of the alphabet is replaced with another letter, number, or symbol. The Pigpen or Masonic Cipher is an early example:
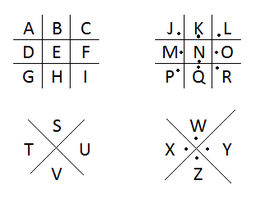
Masonic Cipher – each letter of the alphabet is substituted for a symbol represented by its location within the “boxes.” Sample below:
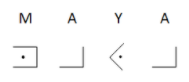
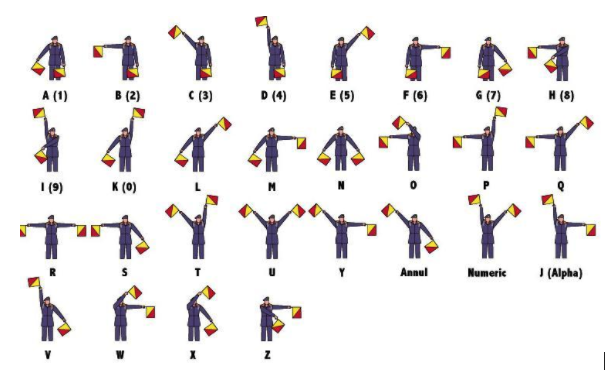
In Semaphore Code the letters of the alphabet are represented by the position of signal flags:
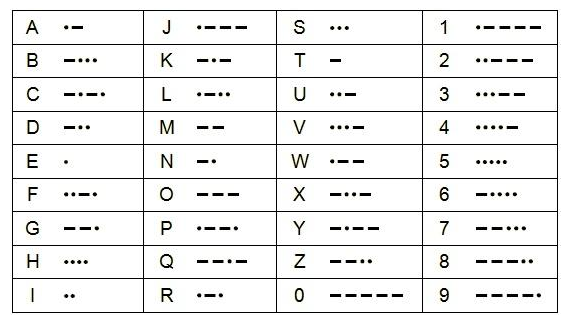
Morse code uses electronic pulses to represent the letters of the alphabet:
The problem with mono alphabetic substitution is that they are relatively easy to crack, or decipher. Given a knowledge of the author’s language, the phenomenon of letter frequency will reveal the secret message.
For example, the letter most commonly used in the English language is E. Therefore, going through a message using mono alphabetic substitution, substituting the letter or number or symbol that occurs most often for an E is the start to decoding the message. The next step is to substitute the second most represented symbol for the second most used letter, which is T. Next, substitute the third most represented symbol for the third most used letter, which is A. Continue for all subsequent letters in order of usage; O, I, N, S, R, H, D, L, U, C, M, F, Y, W, G, P, B, V, K, X, Q, J and lastly Z.
Julius Caesar invented the Caesar cipher (not to be confused with “columnar transposition cipher” or “Caesar’s Box” – unclear if ever actually used by Caesar). In the Caesar cipher, each letter is replaced with another letter that’s a fixed number of positions down the alphabet. The tri-graph pictured below – still in use in modern cryptography – is based on the principle of this simple cipher.

Again, the problem is that any such cipher is easily cracked using the principle of letter frequency analysis. A further means of encryption is required. Modern clandestine communications involve the use of one-time pads, where two parties possess identical pads covered with five-letter groups of random letters. It is (obviously) very important that both parties use identical one-time pads, or the deciphered messages would not make any sense.
Using one-time pads, a message is encrypted by picking a line in the one-time pad (known as the key text). Say:
VAXPM IPIXU QUXIP MAXIU
The message is written in clear text below it:
VAXPM IPIXU QUXIP MAXIU
MEETA TTENT ONIGH TXXXX
(meet at 10 tonight)
For each letter, the key text and plain text character are located in the tri-graph to find the resulting encrypted text.
Because of the symmetric nature of the tri-graph, the encrypted text can be decoded using the same procedure. That is, if a key and encrypted letter is looked up, one will arrive at the decoded letter.
This form of encryption is actually quite strong. Assuming that the pads are truly randomly generated, never reused, and never compromised, the system is unbreakable. To produce such one-time pads, however, requires a national-level intelligence organization. There is a surprisingly simple method to replicate the unbreakable system of one-time pads, known as a ‘Book Code’.
In a Book Code, the parties wishing to communicate clandestinely each possess an identical copy of the same book. It can be any book – a text book, a technical manual, or even a novel – it doesn’t matter. What is crucial is that each copy of the book is of the same edition, because the text of the book will be used in place of the random letter groups of the one-time pad. Each party must know the key, or start point within the book – what page, and what line of text – where the message starts to be encrypted through the tri-graph.
The beauty of the Book Code is that any printed medium can be used – a specific edition of a newspaper, the lettering within an advertisement in a magazine, a series of street signs in a big city; one is limited simply by one’s imagination. As with the one-time pad system, a message encrypted through a Book Code cannot be decoded.
The origins of modern electronic encryption began with the Enigma machine, used by the German forces during World War II. The Enigma machine was an electro-mechanical rotor cipher machine; a combination of mechanical and electrical subsystems, consisting of a keyboard; a set of rotating discs called rotors arranged adjacently along a spindle; and one of various stepping components to turn at least one rotor with each key press.

The details of the Enigma system, along with the concepts of modern public key cryptography, are beyond the scope of this post. The intent here is to present basic types of ciphers and codes, and the principles upon which they are. Basic tricks of the trade to be placed in your tool box to be used when and if necessary. And in all your endeavors, remember this: if you ain’t cheating, you ain’t trying, and if you get caught, you ain’t cheating hard enough.
Sean Linnane is the pseudonym of a retired Special Forces career NCO (1st SFG, 3d SFG, 10th SFG). He continues to serve as a security professional on six continents.
[revad2]



